Ah, the blockchain! A realm where the promise of decentralization dances tantalizingly close to the precipice of chaos. In this digital age, we find ourselves beset by the specter of cybersecurity risks, lurking like a shadowy figure in a Dostoevskian novel, ready to shake the very foundations of trust in our beloved DeFi platforms, cryptocurrencies, and wallets. 😱
Yet, lo and behold! The blockchain, that resilient creature, has learned from its many misadventures, evolving and adapting like a character in a tragicomedy, striving to enhance its infrastructure and restore faith. But, dear reader, let us not be naive; the 51% attack looms large, a formidable threat that haunted many networks between 2018 and 2020, with only a single notable incident in the past year. Let us delve into this security shortcoming, shall we? 🤔
Key Takeaways:
- When one entity or group seizes control, the 51% attack becomes a reality, and oh, what a reality it is!
- Decentralized networks, those fragile constructs, rely on distributed authority, but when one party holds the reins, chaos ensues.
- Double-spending and transaction blocking—two delightful outcomes of a 51% attack, like a tragic twist in a play! 🎭
Understanding the 51% Attack
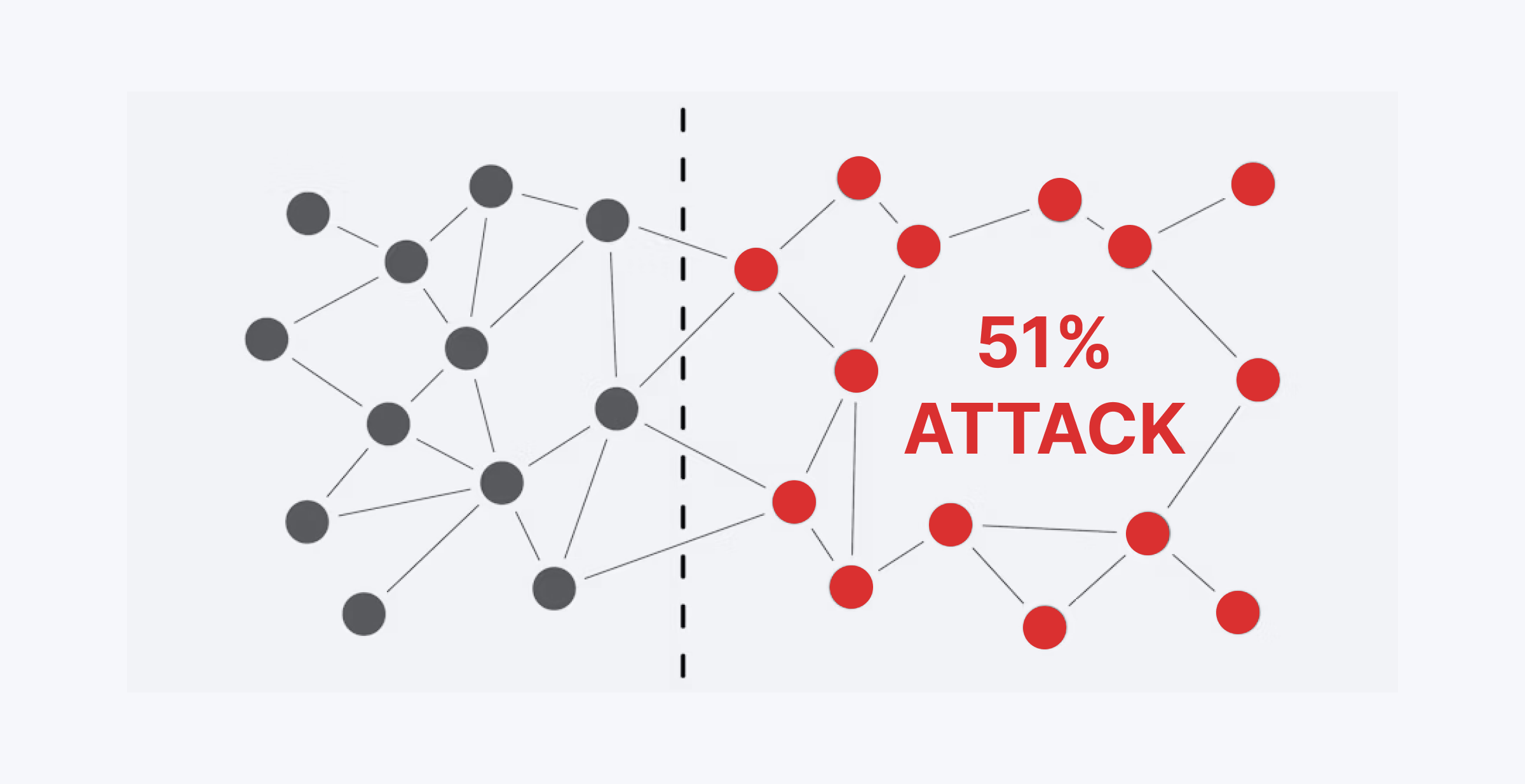
Picture this: a single party, emboldened by greed, gains majority control, wielding the power to dictate the fate of the network. The very essence of decentralization, that noble ideal, crumbles as decisions are made not by the many, but by the few. When one individual or group commands more than half of a blockchain’s mining or staking power, they can rewrite history, preventing new transactions from gaining the sacred confirmations. Oh, the irony! 😅
While some advanced blockchains are designed to resist such breaches, vulnerabilities remain, particularly in the fresh and naive DeFi projects, leading to catastrophic breakdowns. Trust, once shattered, is a hard thing to mend.
Why Does It Happen?
Ah, the motives! These breaches often arise from a desire to disrupt, to gain financial control through double-spending, or perhaps for the thrill of crypto ransoms. Weaker networks, like timid characters in a Dostoevsky novel, are more susceptible to these attacks, as it is far easier to seize majority control.
How 51 Percent Attack Works?
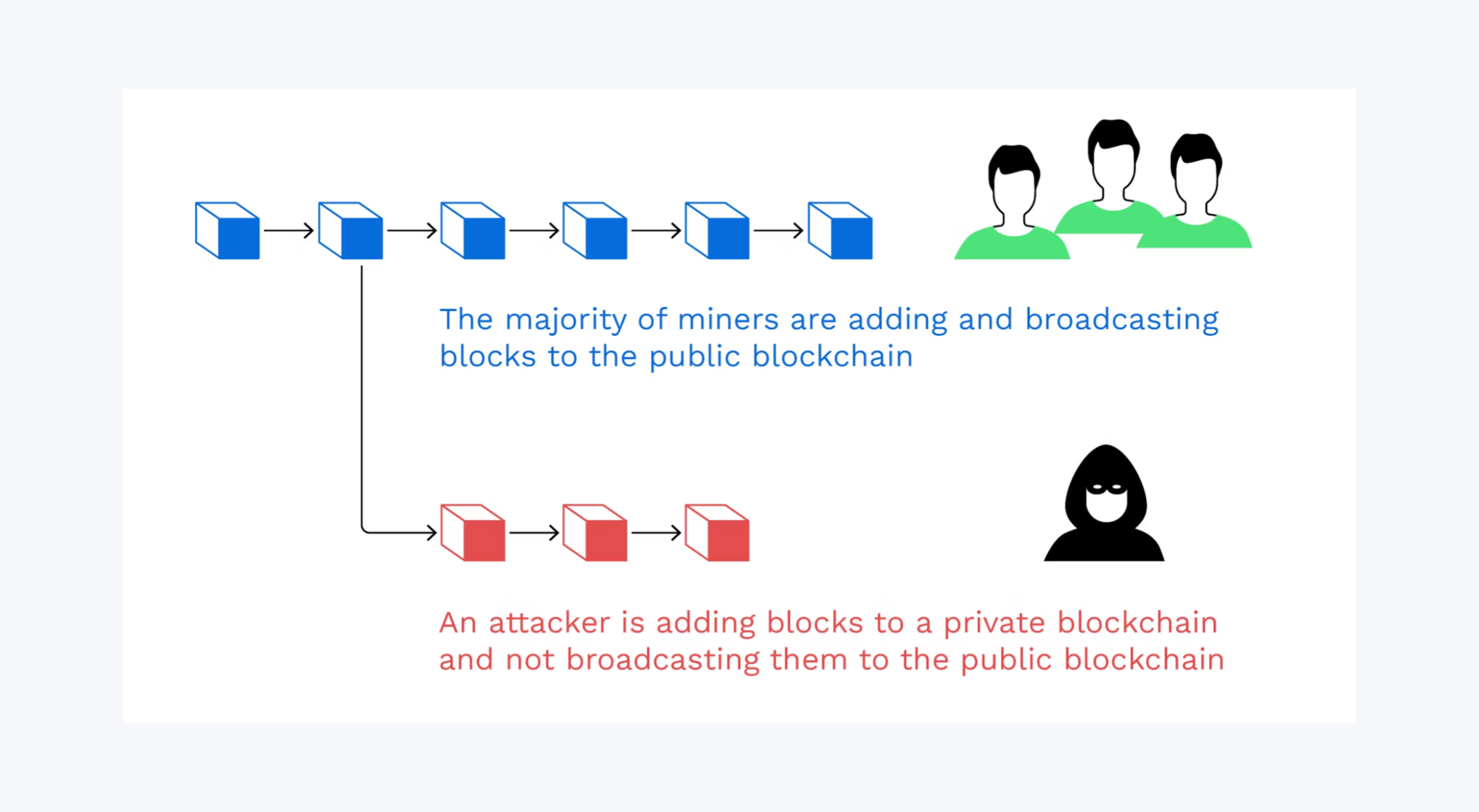
When a malicious party gains control over a blockchain network by 51%, they become the puppet master, dictating actions with a flourish. They complete blocks faster than the legitimate participants, all for a financial advantage. The audacity! This allows them to reverse transactions, leading to the delightful chaos of double-spending. They can block or delay transactions, rendering the network as reliable as a broken clock. ⏰
While they cannot conjure new coins from thin air or tamper with already-confirmed transitions, the shaken trust can ripple through the entire blockchain, affecting the decentralized system as a whole.
Fast Fact
Ah, the cost of 51% attacks! Some nodes, in their cunning, rent hash rates through cloud mining platforms, performing this hack at a fraction of the cost. A true comedy of errors! 😂
Double-Spending
One of the most significant consequences of a 51% crypto attack is double-spending. Imagine, if you will, an attacker spending money from the controlled network to buy a service, only to manipulate their hashing power and reverse the transaction, spending the same coins elsewhere. A true magician’s trick! 🎩✨
In essence, they send cryptocurrency to a merchant, receive goods, and then, with a flick of their wrist, reverse that payment by rewriting the blockchain’s history. Double-spending erodes the credibility of digital currencies, making it vital for blockchain ecosystems to defend against such vulnerabilities with fervor.
Blocking Transactions
The perpetrator can halt payments or delay confirmations, changing network fees or cherry-picking transactions to suit their whims. This selective approval renders transactions pending indefinitely or rejected without reason, massively affecting the network’s efficiency and reliability. A true farce! 🤡
This power could be exploited to damage competitors, create panic, or exert political and financial control over decentralized networks. The drama unfolds!
Cryptocurrency Risks
A 51% attack represents a profound risk that affects users, investors, and developers alike. Financial losses from double-spending and frozen transactions can severely damage blockchains, decentralized exchanges, and cryptocurrencies. The market reacts like a character in a Dostoevsky novel, spiraling into chaos. 📉
Once faith in a network’s integrity deteriorates, its market price can collapse dramatically. After a suspected attack, exchanges require more confirmations to process transactions, sometimes hundreds or even thousands of blocks deep, to prevent double-spending. Small or emerging projects with lower mining or staking participation will suffer financially, limiting their ability to operate and potentially losing clients. A tragic fate indeed!
51% Attacks in PoW Networks
Proof-of-Work systems like Bitcoin are more prone to these attacks due to the nature of their validation process and shared control. In a PoW network, computational power translates to voting rights, and when an attacker controls the majority of the network’s hashing power, they can outpace other miners and earn rewards. A true power play! 💪
Networks with smaller hash rates are more vulnerable, as acquiring sufficient mining power becomes cheaper and easier. Thus, major blockchains involve enormous hash rates, making an attack relatively expensive, while smaller projects remain easy targets. Hence, many PoW chains encourage mining and shared authority to defend against such threats.
51% Attacks in PoS Networks
Proof-of-stake networks, in their wisdom, replace mining with staking, making them more resilient against these attacks, but not entirely foolproof. In PoS networks, staked tokens translate into voting rights, meaning attackers must own the majority of the staked assets rather than computational power. A costly endeavor! 💰
However, if a few large nodes gain collective ownership, PoS networks can become susceptible to governance issues and collusion. Thus, PoS chains rely on good faith and community governance to ensure decentralization and combat takeover attempts.
How to Prevent a 51 Attack in Blockchain Network
Preventing a 51% attack demands a robust technical, economic, and community-driven infrastructure. There is no one-size-fits-all approach, as it is more about implementing proactive layers to maintain integrity, resilience, and trust in decentralized finance. A noble quest! 🛡️
This begins with deciding on the blockchain type, whether it is PoW or PoS. For example, PoS-based chains allocate voting rights based on merit, while PoW networks distribute authority based on network hashrate.

Ultimately, no blockchain is entirely immune to cyber threats. 51% attack prevention requires several proactive measures to reduce the risks:
- Increase Network Participation: Encouraging more miners or validators to join the network distributes power evenly, making it less likely for any single miner to gain majority consensus.
- Implement Checkpointing: Adding frequent checkpoints within the blockchain’s code prevents attackers from rewriting transactions, making double-spending attacks less feasible.
- Economic Penalties: Introducing a clear code of conduct and penalty system in PoS networks ensures all nodes act in good faith. Slashing is a deterring mechanism that punishes actors who break staking rules, cutting their block rewards in case of violation.
- Diverse Mining/Staking Pools: Ensuring decentralization of mining and staking pools prevents one entity from dominating activities within the ecosystem.
Historical Examples
Ah, the tales of woe! 51% attacks remain one of the most common hacks in cryptocurrency, leading to lost trust and exclusion from major exchanges. Several prominent blockchains have suffered these breaches, revealing weaknesses in both emerging and established systems.
Ethereum Classic, Bitcoin Gold, and Bitcoin Cash are but a few examples of these tragic instances. Let us review how they unfolded and their outcomes.
Bitcoin Gold Attack 2018
In May 2018, Bitcoin Gold (BTG), a fork of the Bitcoin network, fell victim to a brutal 51% attack, where hackers gained sufficient hashing power to double-spend and steal over $18 million worth of BTG. Another successful attack occurred in 2020, resulting in estimated losses of $72,000 worth of BTG. A true tragedy! 😢
Developers attributed the attack to Bitcoin Gold’s relatively low hash rate, which made it an easy target. This highlighted how smaller networks, despite high-profile branding, remain weak without robust decentralization and security. The attackers exploited this vulnerability, creating new blocks and reversing transactions after goods or services had been exchanged, severely damaging BTG’s credibility and value, leading to its delisting from major exchanges.
Bitcoin Cash 2019
In May 2019, Bitcoin Cash (BCH) experienced a majority attack following a network upgrade dispute. This time, two mining pools performed the hack to block an unknown node from gaining unauthorized access. A defensive maneuver, if you will! 🛡️
This breach was caused by two legitimate actors, who briefly seized majority control to prevent network exploitation by a malicious actor. The attack was more a defensive mechanism than an offensive one, yet it highlighted vulnerabilities and how trusted participants can change their behavior.
Ethereum Classic 2020 & 2024
Ethereum Classic, that open-source alternate chain, fell victim to multiple hijacks in 2020 and 2024. During these incidents, attackers successfully reorganized thousands of previous block information, resulting in significant double-spending instances, taking advantage of the network’s low hash rate and staking participation. A tragic fate for a once-promising network! 😔
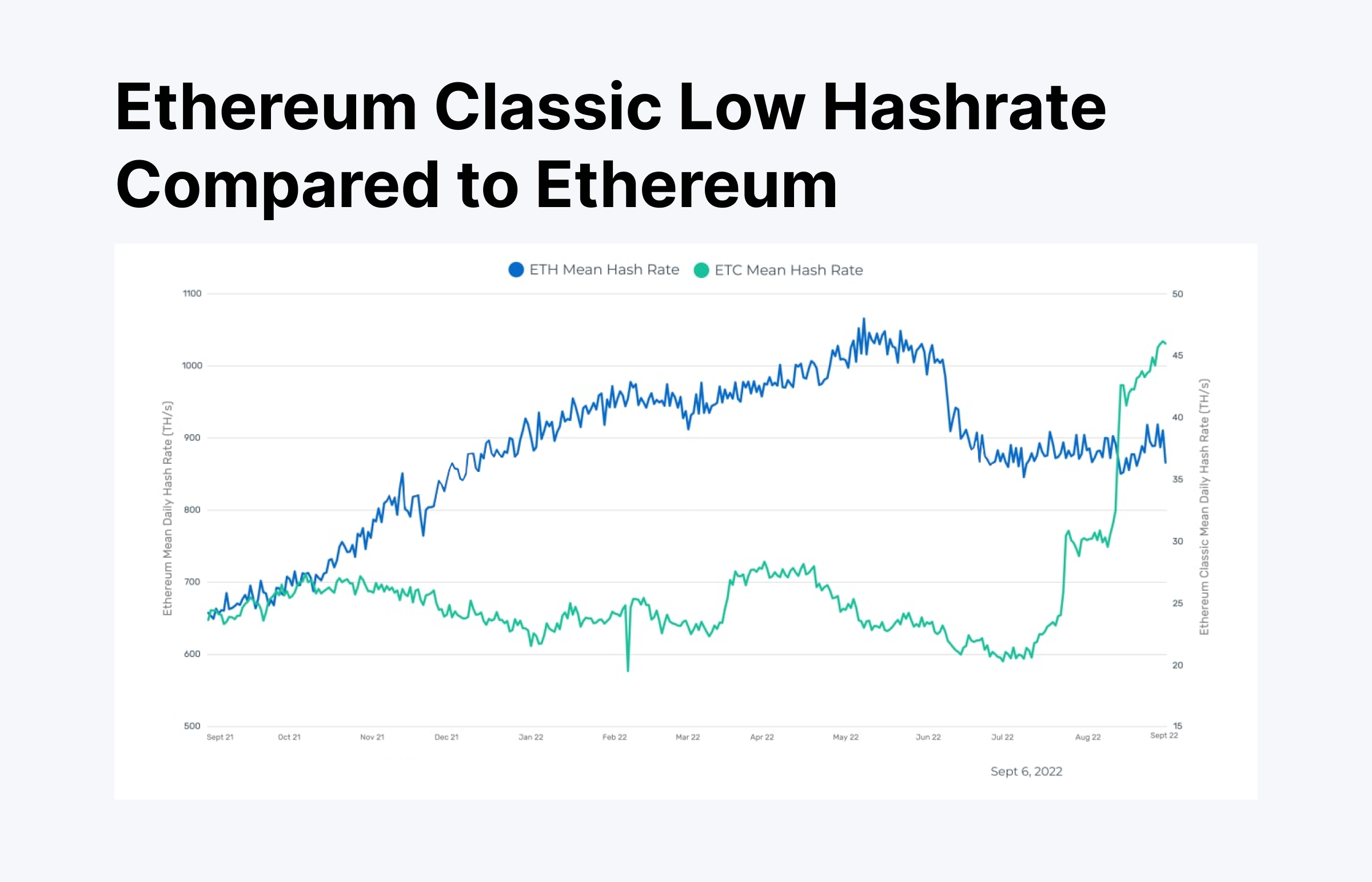
The network was a target of organized hacks that happened repeatedly between 2019 and 2024, with some attacks occurring three times a year, causing long-term reputational damage.
Conclusion
The 51% attack remains one of the most serious threats to blockchain security. When a single person can dominate a DeFi network, the very foundation of decentralization and shared control collapses like a house of cards. 🃏
While this mostly occurs in emerging networks and those with low mining and staking activities, any blockchain can fall victim to a 51% breach. DeFi projects with high community engagement, advanced technical safeguards, code checkpoints, and clear node policies are more likely to defend against these attacks. While fixing the damage is technically possible, the aftermath can be severe, leaving scars that may never heal.
Read More
- Bitcoin Hits $111K: Is This the Start of a Crypto Comedy Show? 🎭💰
- LINEA’s Wild Ride: From Sky-High to Down in the Dumps 🚀📉
- Bitcoin’s Wild Dance: Fed’s Snip Sends It Soaring, Then Tumbling! 🪙💨
- TRON’s USDT Surge: Billionaire Secrets Revealed! 🐎💸
- Corporate Giants Dive into Bitcoin with $458 Million Bet: Is This the End of Fiat?
- Interactive Brokers: Crypto Cash, Now With More Sarcasm!
- Bitcoin to Moon? Tom Lee’s Wild Predictions and a Universe of Imbalance 🚀
- Bitcoin’s Droll Dance: Profits Plummet While Prices Prance! 💃🕺
- 11,000 Wallets Fight for NIGHT Tokens in Cardano Airdrop-And It’s a Disaster 🤦♂️
- Dogecoin’s Journey to $5: The Hilarious Truth Behind the Hype! 🚀💰
2025-05-21 11:55