Background of Coinbase’s May 2025 breach
On May 11, 2025, Coinbase, the cryptocurrency exchange that’s practically a household name (if your household is filled with tech nerds), received an unsolicited email from a mysterious threat actor. They claimed to have sensitive customer information and demanded a ransom of $20 million. Because, you know, who doesn’t love a good ransom note? 😏
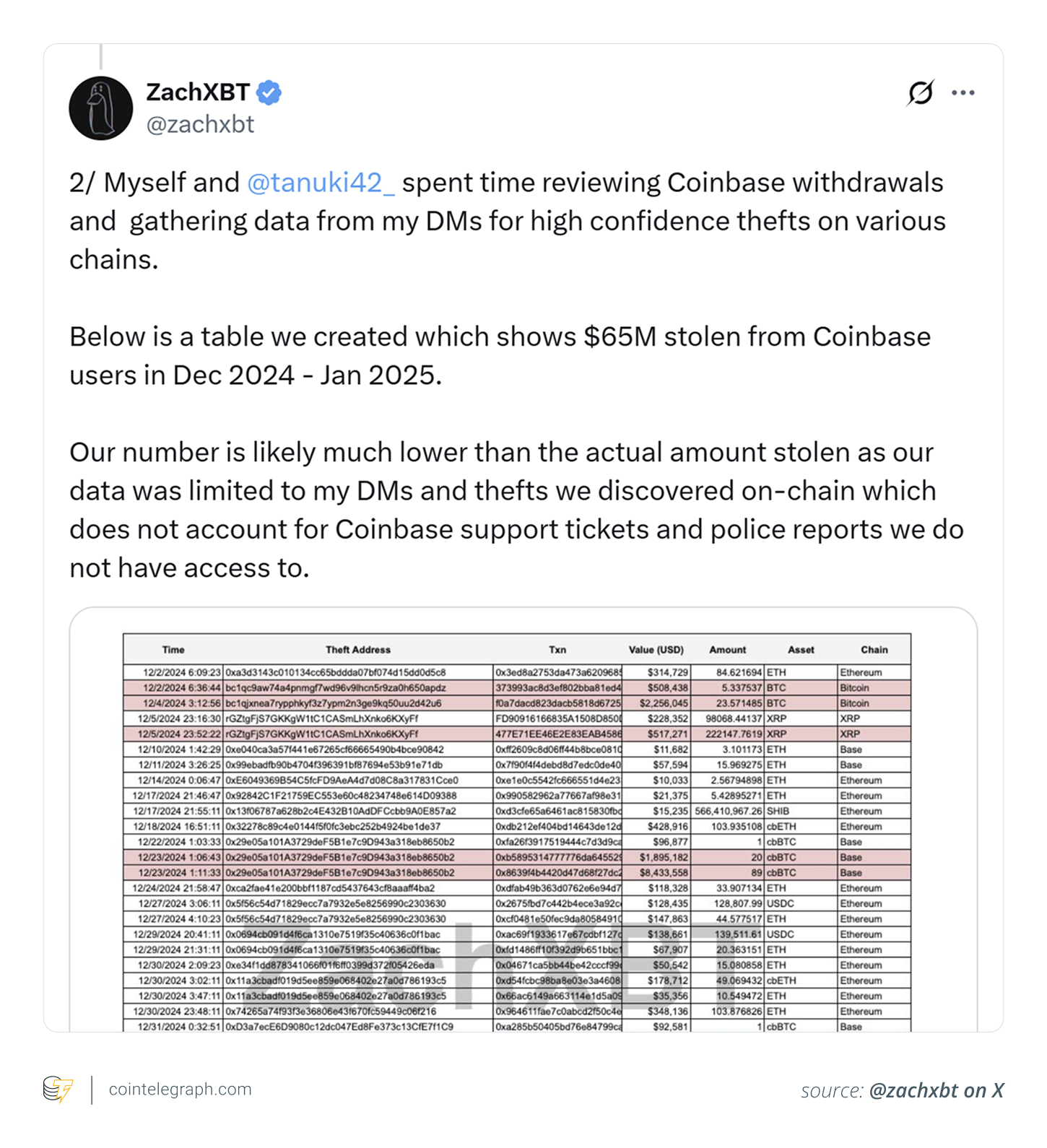
Now, before we dive into the breach, let’s ponder how this happened at a company that spends millions on cybersecurity each month. In February, blockchain investigator ZachXBT reported a spike in thefts involving Coinbase users. He pointed fingers at aggressive risk models and noted Coinbase’s spectacular failure to prevent $300 million in annual losses from social engineering scams. Oops! 😬
A table shared by ZachXBT on X revealed that $65 million was stolen from users between December 2024 and January 2025. He also hinted that the real losses could be even higher, as his data only came from his DMs about on-chain thefts, excluding Coinbase support tickets and police reports he couldn’t access. Classic! 📉
On May 11, the nightmare became a reality when Coinbase confirmed in a blog post that account balances, ID images, phone numbers, home addresses, and partially hidden bank details were stolen. Talk about a bad day at the office! 😱
Then, on May 21, the same threat actor decided to have a little fun and swapped about $42.5 million from Bitcoin (BTC) to Ether (ETH) via THORChain. They even had the audacity to write “L bozo” in the transaction input data, followed by a meme video of NBA player James Worthy puffing on a cigar. Because nothing says “I’m a criminal” like a good meme! 😂

What happened: Timeline of the Coinbase breach
The 2025 Coinbase breach wasn’t your run-of-the-mill crypto hack involving smart contracts or blockchain vulnerabilities. No, it was more like a classic IT security failure, complete with insider manipulation, corporate espionage, and an extortion attempt. Grab your popcorn! 🍿
Here’s how the drama unfolded:
- Insider recruitment and information theft began: Cyber attackers recruited overseas customer service agents (based in India) working for Coinbase. These insiders were paid to leak sensitive customer data and internal documentation. Because who doesn’t want a little extra cash for selling out their employer? 💰
- Security detection and employee termination: Coinbase’s internal security team eventually caught wind of the suspicious activity. The involved staff were swiftly terminated, and the company alerted affected users. Just 69,461 accounts were impacted, but hey, it’s the thought that counts, right? 🙄
- Extortion attempt via email (May 11, 2025): Coinbase received an unsolicited email claiming to possess internal system details and personally identifiable information (PII). This was later confirmed as credible in an 8-K SEC filing. Surprise! 🎉
- Coinbase refuses to pay $20M ransom (May 14, 2025): Instead of caving in, Coinbase flipped the script. They reported the breach to law enforcement, disclosed it publicly, and offered a $20 million reward for information leading to the attackers’ arrest. Talk about turning defense into offense! 🥊
- Breach disclosure and public notification: Shortly after the SEC filing, Coinbase publicly confirmed the breach, clarifying the scope and nature of the attack. A data breach notification was filed with the Maine Attorney General’s office, officially stating 69,461 users were affected. Because transparency is key, right? 🔑
This timeline shows how a crypto company responded differently to an attempted cyber-extortion, with transparency, resistance, and bold countermeasures. Maybe this will change how companies respond to cyber threats in the future. Or maybe not. 🤷♂️

Did you know? North Korea’s Lazarus Group has stolen over $6 billion in crypto since 2017, including a record-breaking $1.46 billion from Bybit in 2025. Just a casual Tuesday for them! 😅
What data was compromised in the Coinbase data breach in 2025?
According to a notification letter issued by Coinbase, attackers sought this information to launch social engineering attacks. The stolen information could help them appear credible to victims and possibly convince them to move their funds. Sneaky, right? 😈
Coinbase detailed what the threat actors accessed and what they couldn’t. Let’s break it down:
What attackers got
- Name, address, phone, and email
- Government-ID images (e.g., driver’s license, passport)
- Masked Social Security (last four digits only)
- Account data (balance snapshots and transaction history)
- Masked bank account numbers and some bank account identifiers
- Limited corporate data (including documents, training material, and communications available to support agents)
What attackers couldn’t get
- Login credentials or 2FA codes
- Private keys
- Access to Coinbase Prime accounts
- Any ability to move or access customer funds
- Access to any Coinbase or Coinbase customer hot or cold wallets
Did you know? In 2022, Crypto.com lost $30 million from 483 accounts. Initially, they claimed no funds were stolen, but later admitted the breach and refunded victims. Transparency is the name of the game! 🎭
How Coinbase responded to the 2025 criminal data breach
- Refusal to pay ransom: Coinbase declined the $20 million ransom demanded by the attackers. Instead, they established a $20 million reward fund for information leading to the arrest and conviction of those responsible. Take that, criminals! 💪
- Customer reimbursements: The company committed to reimbursing customers who were deceived into sending funds due to the breach. Estimated costs for remediation and reimbursements range between $180 million and $400 million. Cha-ching! 💸
- Theft protection services: The company is providing all affected individuals with one year of complimentary credit monitoring and identity protection services. This includes credit monitoring, a $1 million insurance reimbursement policy, identity restoration services, and dark web monitoring. Because who doesn’t want to know if their info is being sold on the black market? 🕵️♂️
- Enhanced customer safeguards: Affected accounts will require additional ID verification for large withdrawals, including mandatory scam-awareness prompts. Better safe than sorry! 🚨
- Strengthened support operations: Coinbase is opening a new support hub in the US. They’ve implemented stronger security controls and monitoring across all locations to prevent insider threats. Because trust, but verify! 🔍
- Collaboration with law enforcement: The company is cooperating closely with US and international law enforcement agencies. Insiders involved in the breach were terminated and referred for criminal prosecution. Bye-bye, bad apples! 🍏
- Transparency and communication: Coinbase immediately notified affected customers once the breach was recognized. They are providing ongoing updates about the breach and the steps being taken to address it. Communication is key, folks! 📣
These measures reflect Coinbase’s commitment to customer protection and its proactive approach to cybersecurity challenges. Because nothing says “we care” like a good PR strategy! 📰
Did you know? Crosschain bridges, like Nomad Bridge, lost $190 million in 2022 due to complex smart contract vulnerabilities. These bridges are hacker favorites because they store massive crypto assets. It’s like leaving your wallet on the table at a bar! 🍻
How to stay safe in the event of Coinbase-like data breaches
In the wake of large-scale data breaches of crypto platforms, you should take proactive steps to protect yourself from social engineering attacks. Because let’s face it, nobody wants to be the next victim! 🙈
Here’s how you can stay safe:
- Never share sensitive information with impersonators: Scammers often pose as support staff or security agents after a breach. They may push you to move funds to crypto wallets they share with you or reveal sensitive information. Remember, no crypto exchange will ask you to transfer crypto to a “new” or “safe” wallet. Just say no! 🚫
- Turn on allow-listing of wallet addresses: Some exchanges provide this feature, which restricts withdrawals to pre-approved wallet addresses you fully control. This prevents unauthorized transfers even if your account is compromised. Safety first! 🔒
- Enable strong 2FA: For 2FA, use a hardware security key or a trusted authentication app. Avoid relying on SMS-based 2FA, which is vulnerable to SIM-swapping attacks. Because who needs that kind of drama? 📱
- Be cautious with unsolicited communication: Hang up immediately if someone calls claiming to be from a crypto platform and asks for security credentials or requests asset transfers. Do not respond to unknown texts or emails with your personal information. Better safe than sorry! 📞
- Lock first, investigate later: If anything feels suspicious, lock your account immediately through the app or platform and report the incident to customer support via official channels. Trust your gut! 🛑
- Stay informed: Regularly review security tips and updates from your crypto services to recognize and avoid evolving scam tactics. Knowledge is power! 📚
Read More
- Gold Rate Forecast
- Brent Oil Forecast
- Is Now the Time to Buy Bitcoin? Shocking Market Signals Unveiled!
- Circle Seeking at Least $5,000,000,000 for Coinbase Acquisition, Potentially Nixing IPO Plans: Report
- Bitcoin’s Plunge: Are Traders Running for the Hills? 🤑💨
- Bitcoin’s Wild Ride: Is It a Rally or Just a Bunch of Greedy Investors? 🤔💰
- XRP: The Calm Before the Storm?
- Pi Coin Plunges 21% After Consensus 2025 — What Could Possibly Go Wrong? 🚀🤡
- Suspected Team Wallet Sent $47M of TRUMP to Crypto Exchanges: Dump Incoming?
- BitMine’s 4M ETH Hoard: Stock Valuation Shenanigans 💰💸
2025-05-28 20:04