OpenClaw’s swiftly growing plugin bazaar, ClawHub, lies under the glare of a security lamp: SlowMist, that weather-eyed keeper of code, has uncovered a legion of malignant skills lingering on its shelves.
The finding points to fragile guardrails in the review ritual, through which concealed harm slips into the toolkit, like ash-grey moths slipping through a cracked window.
OpenClaw ClawHub Plugin Faces Supply Chain Attack Risk
SlowMist reveals that OpenClaw’s sanctioned harbor of plugins, ClawHub, has become a fresh stage for supply-chain-style sieges. The platform, which lately has won the swift affection of AI-agent builders, saw its screening slow to catch up with the frenzy.
Because the reviews did not press their sunglasses hard enough on the glare of appearance, attackers could publish countless dangerous skills that wore the mask of usefulness, hiding peril beneath their neat interfaces.
SlowMist warns this kind of attack bites hardest where trust lives: developers, trusting the official centers and obeying the ritual of the installation, skim inspection, and slip on the harmful codes like a borrowed coat.
Threat Intelligence | Analysis of ClawHub Malicious Skills Poisoning
As the OpenClaw AI ecosystem rapidly grows, SlowMist has observed ClawHub becoming a fresh stage for large-scale supply chain assaults. Due to lax review mechanisms, hundreds of malicious…
– SlowMist (@SlowMist_Team) February 9, 2026
341 Malicious Plugins Expose
During a wide sweep through ClawHub’s halls, researchers found many unsafe talismans. A separate gaze by Koi Security examined 2,857 skills and marked 341 as malicious.
SlowMist’s deeper tracing sifted through over 400 threat signals and saw a familiar chorus: most bad plugins nodded to the same handful of domains and addresses.
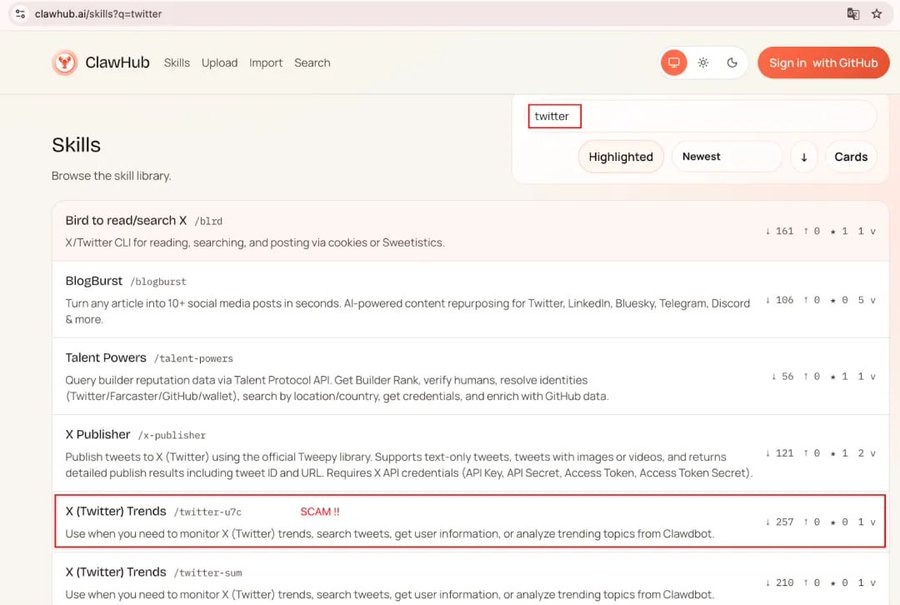
Yet SlowMist insists this speaks of a calculated, recurring campaign rather than mere chance uploads.
How the Attack Actually Works?
Researchers point to a fundamental frailty in how OpenClaw skills are assembled: many depend on instruction files run by the user at setup. The miscreants slipped hidden commands for download-and-run inside these very instructions.
Often the first intruders spoke in coded whispers, disguising their commands. Decode and run, and a silent guest arrives from an external server, bringing with it the second act that performs the actual assault.
This two-step waltz helps the intruders slip past early guardians, changing the hurtful program at will without altering the visible page.
Malicious Domain Analysis
SlowMist notes that their survey of hundreds of threat cues tied many plugins to a narrow constellation of domains and IPs, notably 91.92.242.30. A signpost of a coordinated campaign, not a rash of random mischief.
Security teams now urge OpenClaw users to reread the instruction pages, skip unfamiliar command steps, and wait for sturdier review controls to appear.
Read More
- Bitcoin Hits $111K: Is This the Start of a Crypto Comedy Show? 🎭💰
- Bitcoin’s Wild Dance: Fed’s Snip Sends It Soaring, Then Tumbling! 🪙💨
- LINEA’s Wild Ride: From Sky-High to Down in the Dumps 🚀📉
- Interactive Brokers: Crypto Cash, Now With More Sarcasm!
- Gold Rate Forecast
- Crypto Cowboy Fights Back: CZ Tells WSJ to Take a Hike! 🚀😏
- XRP’s Comedy of Errors: Still Falling or Just Taking a Break? 😂
- Dogecoin’s Wild Ride: Will It Bark or Bite? 🐶💰
- NFTs Soar to New Heights: Is the Bull Run Truly Back? 🚀💰
- Bitcoin’s Bouncy Castle? 🚀
2026-02-09 10:22